SchoolProtect offers a highly flexible web filtering system designed to allow establishments and groups, such as MATs, to have access to local filtering settings.
Filtering is delivered to all your establishment's IP addresses by default. This can be modified by adding USO-based per-user filtering or AD-linked per-user filtering, as required by your establishment.
SchoolProtect functionality: Overview
When a device accesses the internet, it is filtered by the filtering policy which can be managed by the filtering admin. Filtering policies consist of a combination of items including the following which are defined as either allowed or blocked/denied: •Categories of websites •A Local List containing URLs & other entry types •Bundles, which are containers for URLs & other entry types that can be used across multiple policies
All websites are placed into categories by the filtering engine. Adding exceptions for specific URLs and other entries, allows you to override category definitions and give access to a resource whose category is blocked or to block a resource whose category is allowed. A common practice is to block a category of websites but allow a specific website (or several) in that category. For example you may want to allow access to YouTube but not all video streaming websites.
Order of processing When visiting a website the system will perform a check on the policy being used to see whether the website should be allowed or denied. There are a number of different ways websites are allowed or denied. These are: •System List - the global allow/deny list •Local List - the allow/deny list for the establishment •Bundles - containers of URLs that can be created by your establishment, a group you are part of or at the system level. •Categories of websites.
These work on a priority system. Entries in the system list has a higher priority than the local list, the local list has a higher priority than bundles & bundles have a higher priority than category definitions. So for example, if something is allowed or denied in the system list, set by the service provider, it can not be overruled.
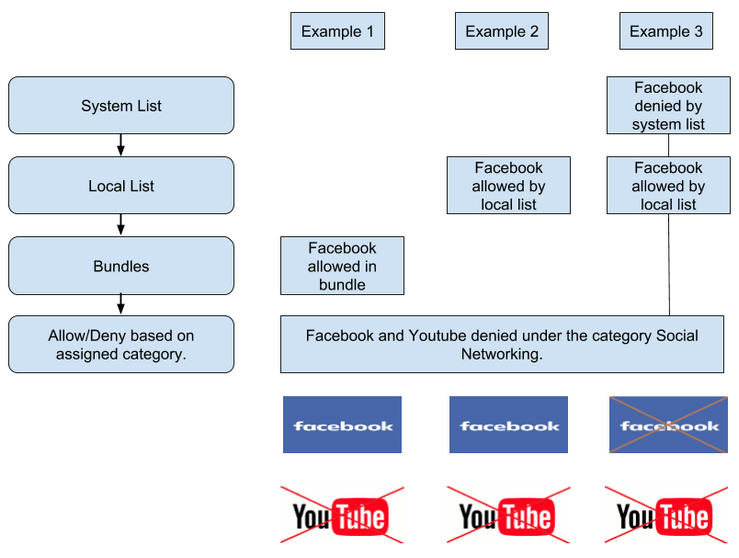
The following example demonstrates how the above works.
In this example, when a request is made, you can see that: •In Example 1, Facebook would be allowed as it's been allowed in a bundle. YouTube is denied by the Category 'Social Networking'. •In Example 2, Facebook would be allowed as it's been allowed in the local list. YouTube is denied by the Category 'Social Networking' •In Example 3, Facebook would be denied as that's been set in the system list, which has priority over the local List allow. YouTube is denied by the Category 'Social Networking'
It's important to keep in mind the above when configuring SchoolProtect or troubleshooting an issue.
Important information on using SchoolProtect with a local firewall or proxy Local firewall users If your school is using its own local firewall in addition to the service provided firewall, and are using this firewall to carry out NAT, SchoolProtect policies can only be configured for the supplied internal IP addresses - as these are the ones the filtering system will see. Per-user filtering is also not available in such circumstances as the system is not able to identify individual users' IP addresses in order to deliver a specific policy to a specific user. Local proxy users If your school is routing all its traffic through an internal proxy or caching device, only one policy can be assigned to the specific IP address(es) belonging to that device. Per-user filtering will also not work, even if configured. Any traffic bypassing this proxy will however work as configured. |
Flexibility •Each establishment can create the filtering environment it requires. •If a school does not enable local filtering it will still be filtered by a system-level filtering policy. Selection of filtering methods •Filtering can be done by applying policies to IP addresses or directly to users (user-based filtering) or via a combination of the two methods. •IP address filtering is done as a default and such filtering policies will always be running. •Per-user filtering can be done via USO users or by AD security groups. Each one requires the relevant elements to be set up. •A time-based element can be added to each policy group to ensure that a policy targeting a particular set of users can change according to requirements at different times of day. Policy management options •Each establishment can create any number of policies and policy groups, as needed. •Policies can contain allow and block lists which are specific to the policy. •Bundles of allowed and blocked items can be linked to multiple policies. This saves administration time and allow changes to filter through dynamically. •A group of schools such as a MAT, federated schools or even schools looked after by the same support company can make use of management features that make administration quick and efficient. Central management tools •The system is configured with a selected set of rules to comply with IWF (Internet Watch Foundation) and Home Office banned content as well as sites related to all aspects of network security. •The system offers users some pre-configured, commonly used bundles of sites that can be easily added to your policies if desired. •Multi-establishment administrators can switch easily between establishments, create centrally managed settings and copy settings between establishments to speed up everyday tasks. Reporting •All online surfing activity is logged and can be reported on in different ways. •A variety of reports can be generated. These depend on the type of filtering used. •Where USO per-user filtering is in place, reports can be run after the point a user has logged into SchoolProtect via the browser. •Where Active Directory-linked filtering is in place, reports can show all user activity from the point they log into the domain. |
The system is based on NetSweeper and provides a school centric, user-friendly interface to the functionality it offers. Settings within the system are applied at multiple levels. •Core settings and the overall system is run by Wavenet Education. •Default filtering policies are defined by the service provider for all connected establishments. These are just templates each establishment can then customise. •The system contains a number of items such as categories, URLs which are pre-defined for all establishments. . •Each establishment is filtered by default system settings until local filtering is enabled and configured. •Once local filtering is set up, adding new items to the Allow or Block list is a very quick process. |
Basics •The system is centrally managed and automatically filters all connected establishments. Filtering is always on. •Establishments coming into the system for the first time will have all IP addresses linked to one of the policy groups that is initially inherited from the system settings. •Each establishment can then configure the settings to their own requirements. •Default filtering is applied to IP addresses only. Any type of per-user filtering must first be configured by your establishment. |
Also see: